Note
This configuration is optional and not required to enable trap monitoring. It is only needed to exclude traps from being forwarded to OpsRamp or to include specific traps of interest for forwarding.When you configure the OpsRamp Gateway as an SNMP trap receiver, it processes traps sent from SNMP-enabled devices based on your trap monitor configuration.
- SNMPv2 traps are not encrypted, so the OpsRamp Gateway can directly interpret their Trap OIDs.
- SNMPv3 traps are encrypted, so the OpsRamp Gateway requires the correct credentials to decrypt and interpret the OIDs.
Default SNMPv3 Credentials
By default, the OpsRamp Gateway can process SNMPv3 traps if the remote devices use the pre-defined credentials included in the Gateway. To obtain a list of these default credentials, contact the OpsRamp Support Team.
Add Custom SNMPv3 Credentials
If you do not want to use the default credentials, you can define your own SNMPv3 credentials to process the traps. These credentials must be encoded in Base64.
Format Custom Credentials
- Define your custom SNMPv3 credentials using the following format:
{securityname}###{authProto}###{authPassPhrase}###{privProto}###{privPassphrase}
Example: user6###MD5###abcdef@123###DES###ghijkl@456
- If any of the following fields are not required or should be left empty, use
NONEas the value:- authProto
- authPassPhrase
- privProto
- privPassphrase
Use the following configuration formats for SNMP privacy and authentication protocols:
| SNMP Privacy Protocol | Configuration format |
|---|---|
| DES | DES |
| DES3 | DES3 |
| AES | AES |
| AES128 | AES-128 |
| AES192 | AES-192 |
| AES256 | AES-256 |
| AES192C | AES-192-C |
| AES256C | AES-256-C |
| SNMP Auth Protocol | Configuration format |
|---|---|
| SHA | SHA |
| SHA224 | SHA224 |
| SHA256 | SHA256 |
| SHA384 | SHA384 |
| SHA512 | SHA512 |
| MD5 | MD5 |
Examples:
For SNMPv3 credentials with authentication and privacy (AuthPriv):
snmpusername###MD5###snmpuserauthstring###DES###snmpprivstringFor SNMPv3 credentials with authentication but no privacy (AuthNoPriv):
snmpusername###MD5###snmpuserauthstring###NONE###NONEFor SNMPv3 credentials with no authentication and no privacy (NoAuthNoPriv):
snmpusername###NONE###NONE###NONE###NONE
Example with specific values:
For a device with the following SNMPv3 credentials:
- Username: user6
- Authentication protocol: MD5
- Authentication password: abcdef@123
- Privacy protocol: DES
- Privacy password: ghijkl@456
Use the following custom credential string:
user6###MD5###abcdef@123###DES###ghijkl@456
Username: user6
Auth: MD5
Authorization password: abcdef@123
Privacy: DES
Privacy password: ghijkl@456
Encode the Credentials
After formatting the credentials, convert them to Base64 encoding using a tool of your choice.
Example:
Formatted credentials: user6###MD5###abcdef@123###DES###ghijkl@456
Encoded as: dXNlcjYjIyNNRDUjIyNhYmNkZWZAMTIzIyMjREVTIyMjZ2hpamtsQDQ1Ng==.
Configure SNMPv3 Credentials on the OpsRamp Gateway
You can configure multiple SNMPv3 credentials on the OpsRamp Gateway to enable secure processing of SNMPv3 traps. Follow the steps below based on your OpsRamp Gateway type.
For Classic OpsRamp Gateway
- Log in to the OpsRamp Gateway using the
ruseraccount. - Open the
/opt/gateway/vprobe/conf/snmp_trap_v3_credentials.cfgfile for editing. - Add each Base64-encoded SNMPv3 credential on a new line in the file.
Note: For details on formatting and encoding credentials, see Add Custom SNMPv3 Credentials. - Save the file and restart the vprobe service:
service vprobe restart
The OpsRamp Gateway is now configured to process SNMPv3 traps using the specified credentials.
For NextGen OpsRamp Gateway
- Create a yaml file in the gateway under path /home/gateway-admin (For example, snmp_trap_v3_creds.yml)and pass the snmp_v3 credentials in a below format.
snmp_trap_v3_credentials: |-
Example:
snmp_trap_v3_credentials: |-
base64EncodedCredkey1
base64EncodedCredkey2
base64EncodedCredkey3
Note
Use two spaces to indent the keys under snmp_trap_v3_credentials, and place the authentication_key and privacy_key on separate lines to maintain proper YAML formatting.Copy the
Base64-encodedcredentials and save the file. Note: For details on formatting and encoding credentials, see Add Custom SNMPv3 Credentials.Retrieve the existing chart version by running the following command:
helm list -n <namespace>
Replace <namespace> with your gateway’s namespace. If you don’t have a custom namespace, use default.
Example Output:
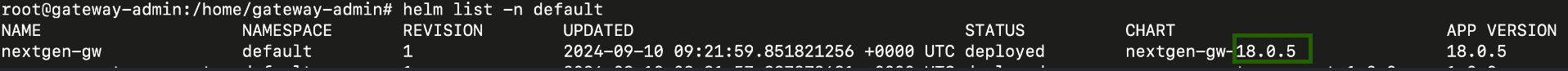
In this output, the chart version is located under the CHART section. For example, if it says nextgen-gw-18.0.5, the version is 18.0.5.
- Update the NextGen gateway helm chart using following command:
helm upgrade nextgen-gw oci://us-docker.pkg.dev/opsramp-registry/gateway-cluster-charts/nextgen-gw --version <current_helm_chart_version> -f <YamlFileName> -n <NAMESPACE> --reuse-values
Example:
helm upgrade nextgen-gw oci://us-docker.pkg.dev/opsramp-registry/gateway-cluster-charts/nextgen-gw --version 18.0.5 -f snmp_trap_v3_creds.yml -n default --reuse-values
Note
The NextGen gateway supports SNMP v3 trap credentials starting with gateway version 17.0.0 or later.- Restart the pod using the following command:
kubectl delete pod nextgen-gw-0 -n <namespace>
Example:
kubectl delete pod nextgen-gw-0 -n default