Simple Network Management Protocol (SNMP) is an application-layer protocol defined by the Internet Architecture Board (IAB) for exchanging management information between network devices. It is a part of the Transmission Control Protocol/Internet Protocol (TCP⁄IP) suite.
SNMP is one of the widely accepted protocols to manage and monitor network elements. Most of the professional-grade network elements come with bundled SNMP agent. These agents have to be enabled and configured to communicate with the network management system (NMS). The SNMP agent is a program that resides on your managed device, packaged within the network element. You have to enable it on your device. It collects the management information from the device locally and provides it to the SNMP manager. These agents could be standard, for example, Net-SNMP or specific to a vendor, such as HP Insight Agent.
SNMP credentials
SNMP uses a password-like authorization known as a community string. When you provide an SNMP credential to a device, it checks to see if the community string matches the community string configured on the device. If the string matches, the device responds to the SNMP query.
Discover the gateway using SNMP
To find the read-only gateway community string, one option is to:
- Log into the gateway WebUI.
- Click SNMP.
Or, you can get the read-only community string by logging into the gateway and reading the string in the /etc/snmp/snmpd.conf file.
You can change the community string to a name of your choice.
Multi-credential functionality
SNMP multi-credential functionality allows you to discover network resources using multiple credentials using a single discovery profile. You can create or use multiple credential sets if you are using a gateway to discover your resources.
For example, a printer uses SNMPv2c credential type and a Cisco router uses SNMPv3 credential type. In such a case, you need to create two discovery profiles. With SNMP multi-credential functionality, you can create one discovery profile and use both the credential sets.
The gateway discovers devices with the credentials, sequentially, as the credentials were entered when a Discovery Profile was created at the time of the first scan. After successful discovery, the gateway remembers resources and their credentials for subsequent discovery.
Multi-credentialed, SNMP-enabled devices have the following advantages:
- Reduces the effort of creating multiple discovery profiles.
- Reduces time for manually traversing through multiple discovery profiles to discover a network resource.
- Scans and discovers a subnet with multiple SNMP community strings.
- Discovers network resources working on different SNMP versions.
SNMP field values
The following provides information on configuring the SNMP fields for creating an SNMP credential set.
SNMPv1 and SNMPv2
| Field | Value | Description |
|---|---|---|
| Port | 161 | Agent receives requests on UDP port 161. |
| Community | N/A | Read-only community string. |
SNMPv3
SNMPv3 is a user-based security model. It provides secure access to the devices by combining authenticating and encrypting packets over the network. The security features provided in SNMPv3 are message integrity, authentication, and encryption.
| Field | Value | Description |
|---|---|---|
| Port | 161 | SNMP Agent port. The default port is 161. |
| Context | N/A | Specify context name (an octet string) that identifies the collection of management information accessible by an SNMP entity. |
| Security Name | N/A | Enter the name of the user (principal) on whose behalf the message is being exchanged. |
| Security Level |
|
|
| Authentication Protocol |
| Authentication in an SNMPv3 uses an encryption algorithm to determine if the data is from a valid source. The encryption algorithms for authentication:
|
| Authentication Password | N/A | Enter the Authentication password. |
| Confirm Password | N/A | Re-enter authentication password for validation. |
| Privacy Protocol |
| Privacy in SNMPv3 uses an encryption algorithm to encode the contents of an SNMPv3 packet. This encoding is used to verify that the content cannot be viewed by unauthorized entities when routed over the network.
|
| Privacy Password | N/A | Enter the privacy password. |
| >Confirm Password | N/A | Re-enter authentication password for validation. |
| Connection time-out | N/A - Default value: 10,000 milliseconds | Provide a maximum time period for discovery. If the gateway does not get a response from the device after 10,000 milliseconds, it terminates the discovery. |
Note
Before starting the SNMP-based discovery, the gateway will check for the following ports: 22, 80, 135, 443, 3389, and 5900 on the remote resources to ensure that the resource is available for further discovery.SNMP definition requests
You can view and submit SNMP definitions for review.
Only Service Provider (SP) and partner-level users can submit SNMP definition requests. All user levels, including SP, partner, and client, can view existing definitions.
View SNMP definition requests
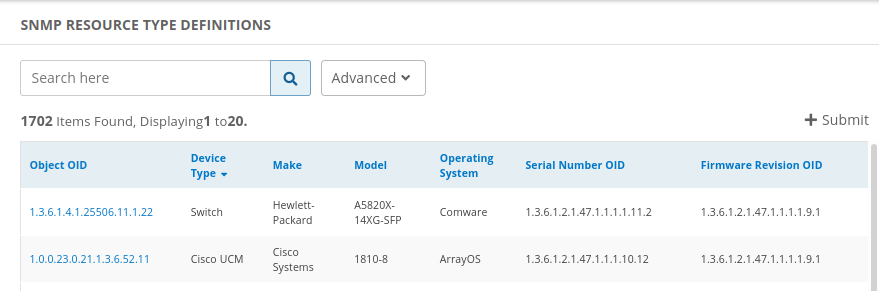
- Go to Setup > Resources.
- Click SNMP Device Type Definitions. This displays the list of available definitions, as shown in the example:
Submit SNMP definition request
Go to Setup > Resources.
Click SNMP Device Type Definitions.
Click the +Submit button.
In the Add SNMP Device Type Definition page, enter the following information:
Device Type Definition:
Field Required Description Object OID Yes Object identifier. Make Yes Choose the make from the drop-down list. Model No If you selected Model, choose the model from the drop-down list. Model OID No If you selected Model OID, enter a model identifier. Device Type Yes Choose a device type from the drop-down list. Operating System Yes Choose an operating system from the drop-down list. Serial Number OID No Serial number identifier. Firmware Revision OID No Firmware revision identifier. Hardware Revision OID No Hardware revision identifier. Software Revision OID No Software revision identifier. SNMP OIDs for Network Interface Information:
Field Required Number of Interfaces No Name No Alias No Index No Type No Speed No Operational Status No Admin Status No Click Cancel to discard your definition or click Submit, which displays the following advisory message:
This definition will reflect on devices only after it is reviewed by a vistara admin. You can check the status on the definition listing page.Click Yes to continue and submit your definition for review.